The Quarantine Zone: Understanding And Managing Suspicious Files On Your PC
The Quarantine Zone: Understanding and Managing Suspicious Files on Your PC
Related Articles: The Quarantine Zone: Understanding and Managing Suspicious Files on Your PC
Introduction
With great pleasure, we will explore the intriguing topic related to The Quarantine Zone: Understanding and Managing Suspicious Files on Your PC. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
The Quarantine Zone: Understanding and Managing Suspicious Files on Your PC
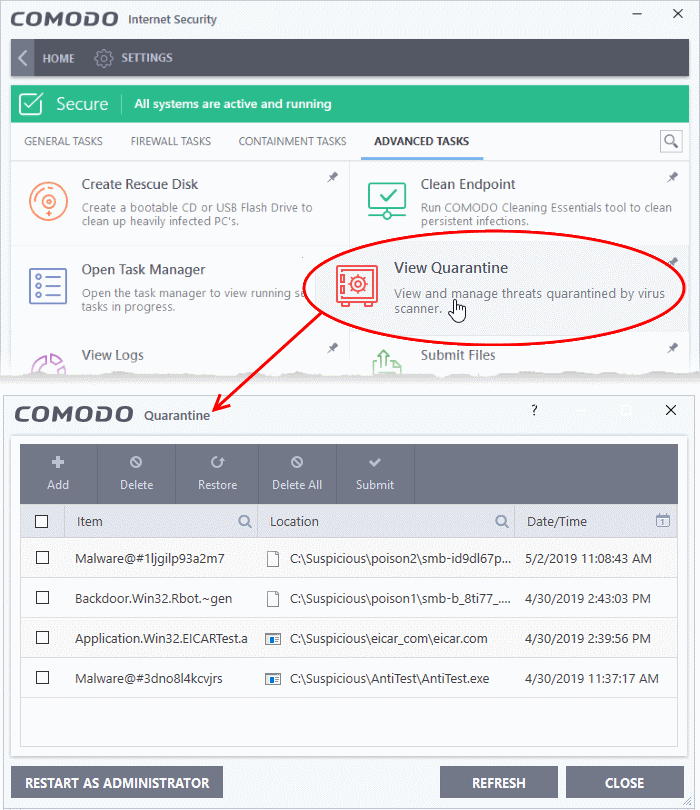
In the digital landscape, where threats constantly evolve and adapt, safeguarding your computer from malicious software is paramount. Antivirus programs play a crucial role in this defense, often employing a "quarantine" mechanism to isolate and neutralize potentially harmful files. This article delves into the concept of quarantine, explaining its purpose, operation, and significance in maintaining a secure computing environment.
Understanding the Quarantine Zone:
The quarantine area within an antivirus program acts as a secure containment zone for files deemed suspicious or potentially harmful. These files are isolated from the rest of your system, preventing them from executing or spreading malicious code. This isolation is crucial as it allows the antivirus software to analyze the file thoroughly and take appropriate action.
The Quarantine Process:
When an antivirus program detects a suspicious file, it initiates the quarantine process. This typically involves:
- Detection: The antivirus software scans files and analyzes their behavior, looking for patterns indicative of malicious activity.
- Isolation: The suspicious file is moved from its original location to the designated quarantine folder.
- Analysis: The quarantined file is subjected to further analysis, including signature matching, behavioral analysis, and sandboxing techniques.
-
Action: Based on the analysis, the antivirus program decides the appropriate course of action. This could involve:
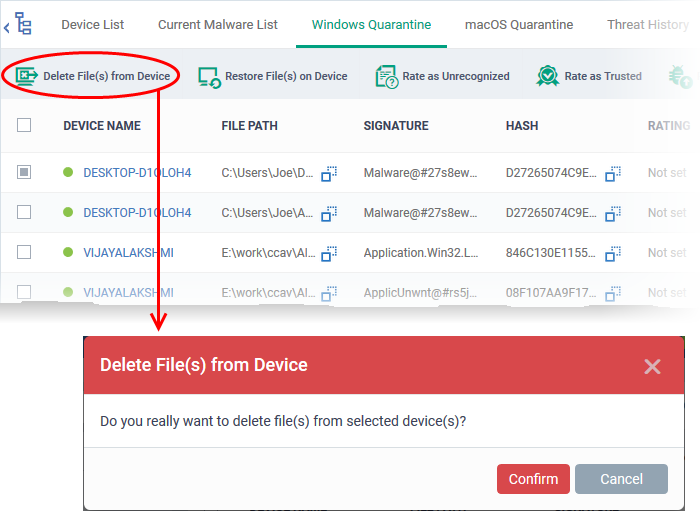
- Removal: The file is permanently deleted.
- Cleaning: The file is sanitized by removing malicious code.
- Restoration: The file is deemed safe and restored to its original location.
- Retention: The file is kept in quarantine for further investigation or for future reference.
Benefits of Quarantine:
The quarantine feature offers several benefits, contributing to a more secure and stable computing environment:
- Protection from Infection: By isolating suspicious files, quarantine prevents them from spreading malware or compromising other files on your system.
- Time for Analysis: Quarantine provides the antivirus software with a safe space to analyze potentially harmful files without disrupting your workflow.
- Remediation Options: Quarantine allows for a range of actions, from removal to cleaning, enabling the most appropriate response to the threat.
- Historical Data: Quarantine can store potentially harmful files for future reference, aiding in the identification and analysis of evolving threats.
Navigating the Quarantine Zone:
While the quarantine zone is a vital security feature, understanding its workings and functionalities is essential.
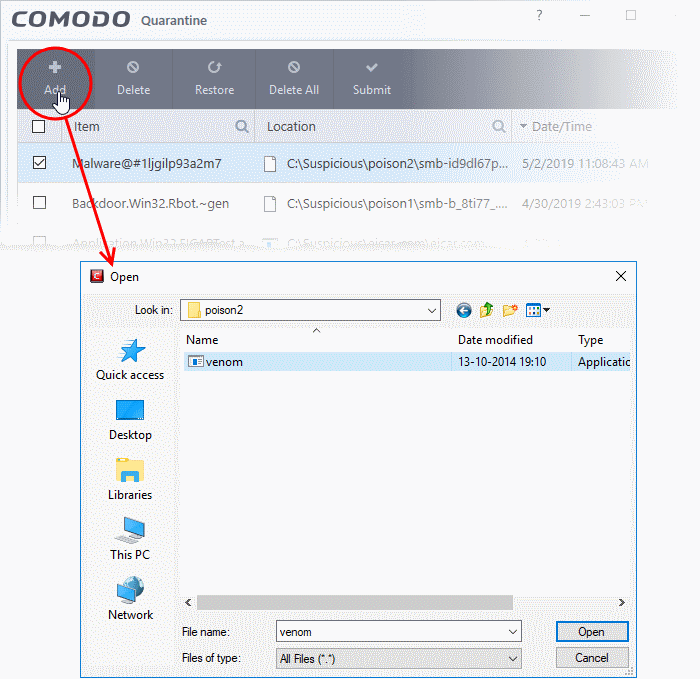
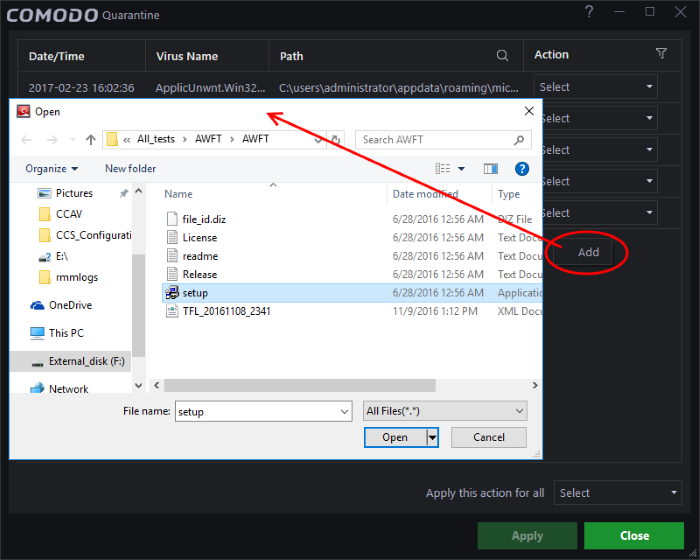
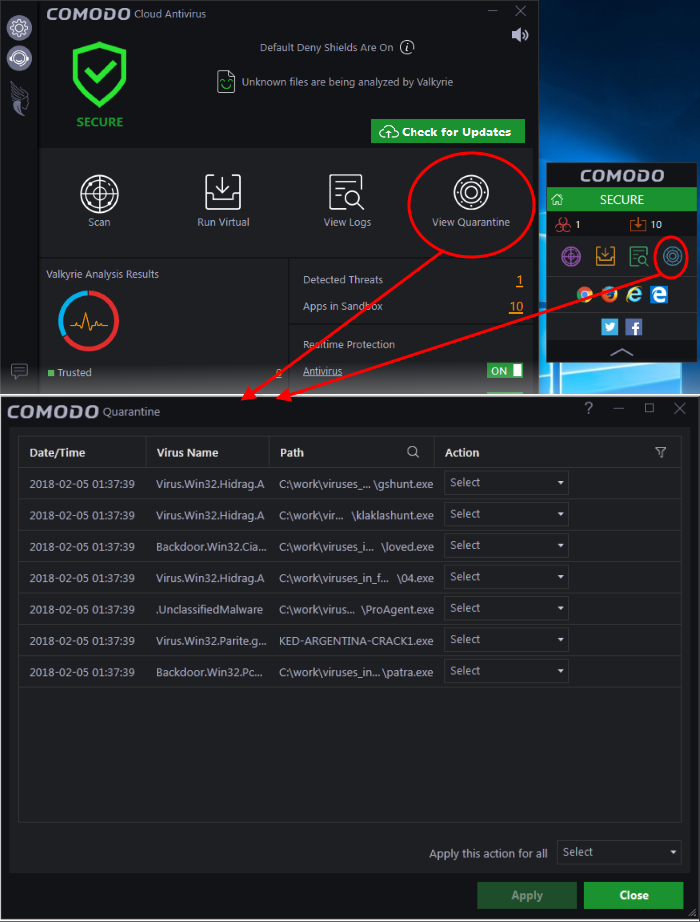
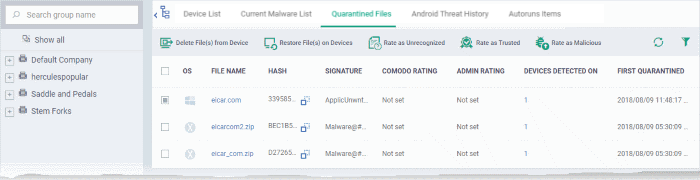
- Access and Management: Most antivirus programs provide a user interface for accessing and managing the quarantine zone. This allows users to review quarantined files, decide on their fate, and manage the quarantine settings.
- False Positives: Occasionally, antivirus programs may misidentify legitimate files as threats, leading to false positives. In such cases, users can typically restore the quarantined file from the quarantine zone.
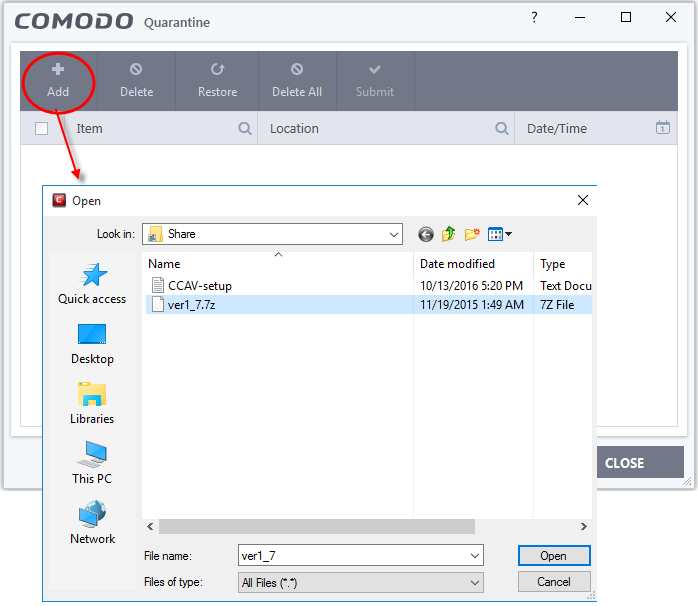
- Manual Quarantine: Some antivirus programs allow manual quarantine of specific files, providing an extra layer of security for files that might be suspicious but not flagged by the antivirus software.
Frequently Asked Questions:
Q: How do I access the quarantine zone in my antivirus program?
A: The location and access method for the quarantine zone vary depending on the specific antivirus software used. Refer to the program’s documentation or help files for instructions.
Q: What happens to quarantined files after a certain period?
A: Most antivirus programs automatically delete quarantined files after a predetermined time, typically a few weeks. This ensures that the quarantine folder doesn’t become overloaded with old files. However, users can typically configure this behavior to suit their needs.
Q: Can I manually restore a quarantined file?
A: Yes, most antivirus programs allow users to restore quarantined files manually. However, it’s crucial to exercise caution when restoring quarantined files, as they might pose a risk to your system.
Q: What should I do if I see a lot of files in my quarantine zone?
A: A large number of quarantined files can indicate a potential security issue. Consider reviewing the files, understanding their origin, and taking appropriate action based on your risk assessment.
Tips for Managing the Quarantine Zone:
- Regularly review the quarantine zone: Periodically check the quarantined files, understanding their origin and nature. This helps identify potential security issues and ensure proper management of the quarantine zone.
- Update your antivirus software: Regularly updating your antivirus program ensures that it has the latest threat signatures and security patches.
- Be cautious with restoring quarantined files: Only restore files from the quarantine zone if you are absolutely sure they are safe.
- Consider using a second opinion antivirus: If you have doubts about a quarantined file, consider using a different antivirus program to scan it for a second opinion.
Conclusion:
The quarantine zone serves as a crucial component of your computer’s security arsenal. By isolating potentially harmful files, it prevents them from executing or spreading malicious code, safeguarding your system from infection. Understanding the workings of the quarantine zone, managing its contents, and implementing best practices for its use are essential for maintaining a secure and stable computing environment. Employing caution, staying informed, and utilizing the tools provided by your antivirus program can significantly reduce the risk of malware infections and protect your valuable data.


Closure
Thus, we hope this article has provided valuable insights into The Quarantine Zone: Understanding and Managing Suspicious Files on Your PC. We thank you for taking the time to read this article. See you in our next article!
Leave a Reply