Safeguarding Your Windows 10: A Comprehensive Guide To Ransomware Protection
Safeguarding Your Windows 10: A Comprehensive Guide to Ransomware Protection
Related Articles: Safeguarding Your Windows 10: A Comprehensive Guide to Ransomware Protection
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Safeguarding Your Windows 10: A Comprehensive Guide to Ransomware Protection. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Safeguarding Your Windows 10: A Comprehensive Guide to Ransomware Protection

In the digital age, where information is paramount and data reigns supreme, the threat of ransomware looms large. This malicious software, designed to encrypt and hold your valuable data hostage until a ransom is paid, poses a significant risk to individuals and organizations alike. Windows 10, despite its robust security features, is not immune to these attacks. Therefore, understanding and implementing effective ransomware protection strategies is crucial for ensuring the safety and integrity of your digital assets.
This comprehensive guide explores the multifaceted world of ransomware protection on Windows 10, providing a detailed understanding of the threats, the vulnerabilities, and the comprehensive strategies for mitigating risks. We delve into the intricacies of preventative measures, proactive security practices, and recovery strategies, empowering you with the knowledge and tools to safeguard your digital environment.
Understanding the Ransomware Threat
Ransomware operates on a simple yet devastating principle: it infiltrates your system, encrypts your files, and demands payment for their decryption. This encryption is often sophisticated, rendering your data inaccessible without the decryption key held by the attackers. The consequences can be dire, ranging from personal inconvenience to crippling business disruptions.
Types of Ransomware Attacks
Ransomware attacks can be broadly categorized into two main types:
- Crypto-Ransomware: This is the most common type, utilizing strong encryption algorithms to render your files unusable. The attackers demand payment, usually in cryptocurrency, to provide the decryption key.
- Locker Ransomware: This type blocks access to your entire system, often by locking the screen or taking control of your mouse and keyboard. The attackers demand payment to unlock your system and restore access.
Common Entry Points for Ransomware
Ransomware can infiltrate your Windows 10 system through various methods:
- Phishing Emails: These emails often contain malicious attachments or links that, when clicked, download the ransomware onto your computer.
- Malicious Websites: Visiting compromised or untrusted websites can expose your system to ransomware infections.
- Exploited Vulnerabilities: Outdated software or operating systems can harbor security vulnerabilities that ransomware can exploit.
- USB Drives and External Devices: Connecting infected external devices to your computer can introduce ransomware.
- Software Downloads: Downloading software from untrusted sources can expose your system to ransomware.
The Importance of Proactive Protection
Proactive measures are the cornerstone of effective ransomware protection. These measures aim to prevent ransomware from ever gaining access to your system, minimizing the risk of infection and data loss.
Key Proactive Measures:
- Regular Software Updates: Keeping your operating system, antivirus software, and other applications updated is essential. Updates often include security patches that address known vulnerabilities exploited by ransomware.
- Strong Passwords: Use complex and unique passwords for all your accounts, including your Windows 10 login. Consider using a password manager to securely store and manage your passwords.
- Enable Two-Factor Authentication: This adds an extra layer of security by requiring a second verification step, such as a code sent to your phone, when logging into accounts.
- Be Wary of Phishing Attempts: Never click on suspicious links or open attachments from unknown senders. Verify the sender’s identity and the legitimacy of the email before taking any action.
- Use a Reputable Antivirus Software: Install and maintain a reliable antivirus program that can detect and remove ransomware threats.
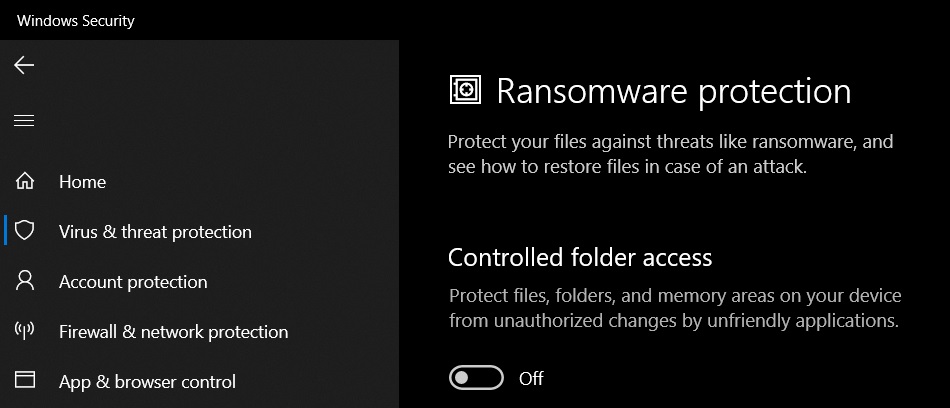
- Enable Windows Defender: Windows 10 comes equipped with built-in antivirus protection called Windows Defender. Ensure it is enabled and regularly updated.
- Back Up Your Data Regularly: Creating regular backups of your important data is essential. Store backups in a separate location, such as an external hard drive or cloud storage, to ensure they are not affected by ransomware attacks.
- Limit User Account Privileges: Restrict user accounts to standard privileges whenever possible. This limits the ability of ransomware to make changes to your system.
- Implement Network Security Measures: Secure your network with a firewall and use strong passwords for all network devices.
- Train Employees: If you are in a business environment, educate employees about ransomware threats and best practices for safe online behavior.
Reacting to a Ransomware Attack
Even with the best preventative measures in place, there is always a chance of a ransomware attack. It is essential to have a plan in place to respond effectively to such an event.
Steps to Take in Case of a Ransomware Attack:
- Disconnect from the Network: Immediately disconnect your infected device from the network to prevent the ransomware from spreading to other devices.
- Isolate the Affected Device: If possible, isolate the infected device from other devices on the network to prevent further contamination.
- Run a Full System Scan: Use your antivirus software to run a full system scan to identify and remove any malicious files.
- Restore from Backup: If you have a recent backup of your data, restore your system from the backup. This will restore your files to their pre-infection state, effectively eliminating the ransomware.
- Contact Your IT Department or Security Professionals: If you are unable to remove the ransomware or restore your system, contact your IT department or cybersecurity professionals for assistance.
- Do Not Pay the Ransom: Paying the ransom does not guarantee that you will get your files back. It may also encourage further attacks and contribute to the ransomware economy.
- Report the Incident: Report the ransomware attack to the authorities, such as your local police department or the FBI.
FAQs About Ransomware Protection
Q: What are the most common signs of a ransomware infection?
A: Common signs include:
- Unusually slow performance: Your computer may become sluggish or unresponsive.
- Missing files: You may notice that some of your files have disappeared or been replaced with empty files.
- Encrypted files: Your files may have unusual file extensions, such as ".locked" or ".encrypted."
- Ransomware demands: You may receive a message demanding payment to unlock your files.
Q: What are the best free antivirus software options for Windows 10?
A: Some highly-rated free antivirus options include:
- Windows Defender: Built-in to Windows 10, it offers basic protection against ransomware and other malware threats.
- Avast Free Antivirus: Provides comprehensive protection, including real-time threat detection and a firewall.
- AVG AntiVirus Free: Offers a good balance of features and performance.
- Bitdefender Antivirus Plus: Provides advanced ransomware protection and a user-friendly interface.
Q: How can I prevent ransomware from spreading to other devices on my network?
A: Implement network security measures such as a firewall and strong passwords for all network devices. Use network segmentation to isolate critical systems and data. Keep your network devices updated with the latest security patches.
Q: How can I recover my files if I have not backed them up?
A: If you have not backed up your files, recovering them after a ransomware attack can be challenging. However, there are specialized data recovery tools and services that may be able to help. Consult with cybersecurity professionals for expert assistance.
Tips for Enhanced Ransomware Protection
- Use a Strong Password Manager: A password manager can securely store and manage your passwords, reducing the risk of using weak or reused passwords.
- Enable File History: Windows 10’s File History feature automatically creates regular backups of your files, allowing you to restore them to a previous state.
- Implement a Zero Trust Security Model: Treat all users and devices as potentially untrusted and enforce strict access controls.
- Educate Yourself and Others: Stay informed about the latest ransomware threats and best practices for preventing attacks. Educate your family, friends, and colleagues about ransomware dangers and how to protect themselves.
Conclusion
Ransomware poses a significant threat to individuals and organizations, demanding a proactive and comprehensive approach to protection. By understanding the vulnerabilities, implementing preventative measures, and developing a robust response plan, you can significantly reduce the risk of falling victim to these attacks. Remember, vigilance, awareness, and proactive security practices are the key to safeguarding your digital assets and ensuring the safety and integrity of your data in the face of evolving cyber threats.

![Ransomware: How to Protection from Ransomware In Windows 10 Windows 10 [January 2020] - YouTube](https://i.ytimg.com/vi/gSakNFc0lWY/maxresdefault.jpg)





Closure
Thus, we hope this article has provided valuable insights into Safeguarding Your Windows 10: A Comprehensive Guide to Ransomware Protection. We hope you find this article informative and beneficial. See you in our next article!
Leave a Reply