Navigating The Labyrinth: A Comprehensive Guide To Ransomware Removal On Windows 11
Navigating the Labyrinth: A Comprehensive Guide to Ransomware Removal on Windows 11
Related Articles: Navigating the Labyrinth: A Comprehensive Guide to Ransomware Removal on Windows 11
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Navigating the Labyrinth: A Comprehensive Guide to Ransomware Removal on Windows 11. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Navigating the Labyrinth: A Comprehensive Guide to Ransomware Removal on Windows 11

The digital landscape is fraught with dangers, and ransomware stands as one of the most potent threats. This malicious software encrypts a user’s files, rendering them inaccessible, and demands payment for their decryption. While the prospect of losing valuable data is frightening, understanding the intricacies of ransomware and its removal on Windows 11 can empower users to navigate this perilous terrain with greater confidence.
Understanding the Enemy: The Nature of Ransomware
Ransomware operates through a cunning strategy. It typically infiltrates a system through various means, including:
- Phishing Emails: Deceitful emails disguised as legitimate communications entice users to click malicious links or open infected attachments.
- Exploited Vulnerabilities: Security flaws in software applications or operating systems provide a backdoor for ransomware to enter.
- Malicious Websites: Compromised websites can host malicious scripts that download ransomware onto unsuspecting visitors’ computers.
- Drive-by Downloads: Visiting infected websites can inadvertently trigger the download and installation of ransomware without user consent.
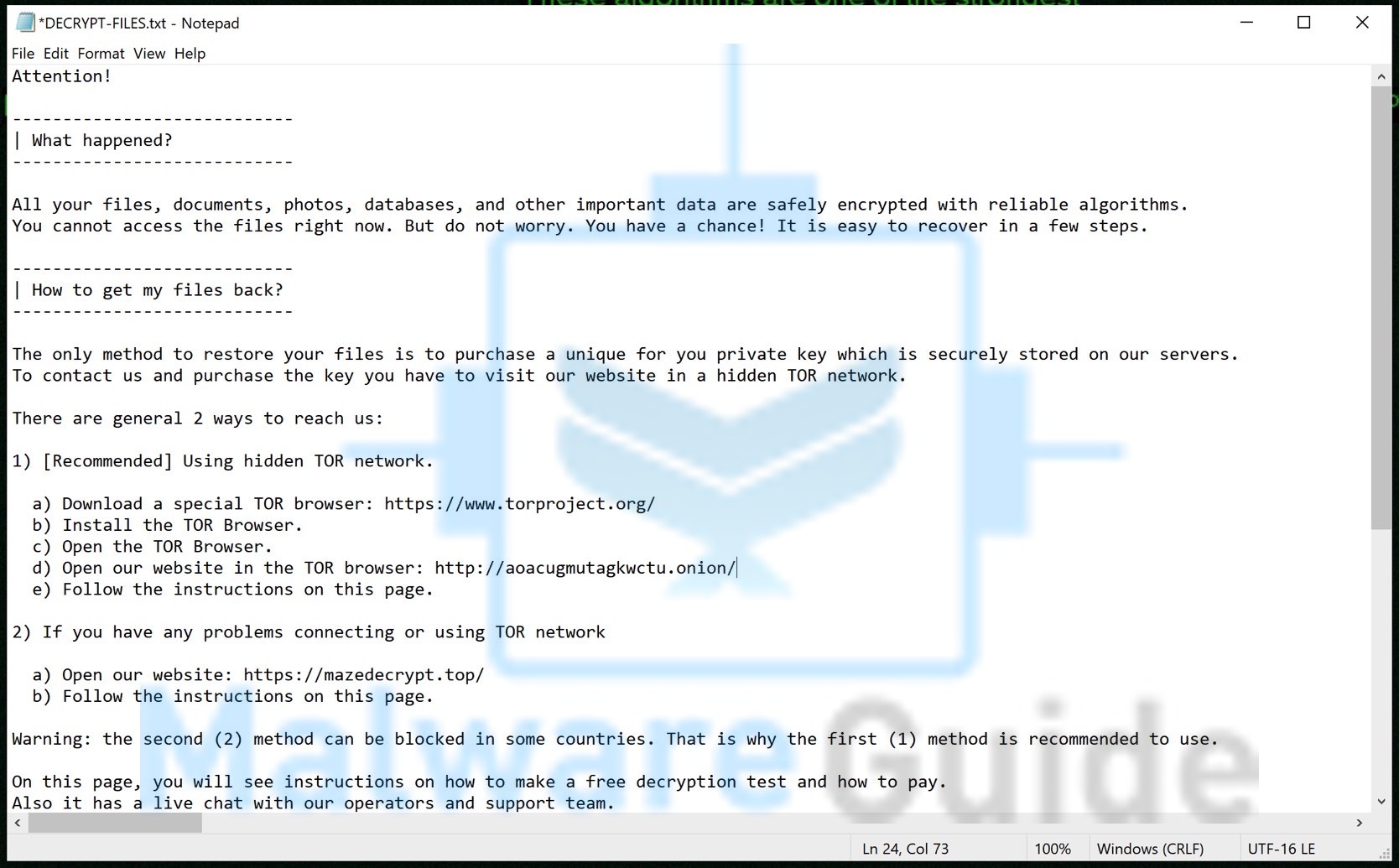
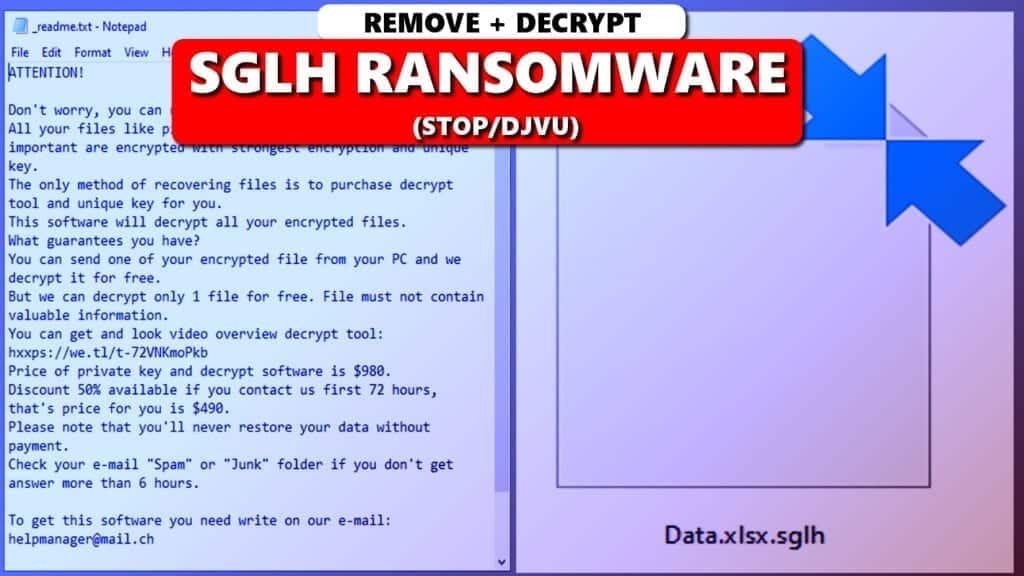
Once installed, ransomware encrypts files using complex algorithms, effectively locking users out of their data. A ransom note, often displayed on the screen or sent via email, demands payment in cryptocurrency, typically Bitcoin, for decryption. The payment process is shrouded in anonymity, making it challenging to track and apprehend the perpetrators.
The Importance of Proactive Measures: Prevention as the First Line of Defense
The most effective approach to ransomware is prevention. By implementing robust security practices, users can significantly minimize the risk of infection.
- Software Updates: Regularly updating operating systems and software applications patches vulnerabilities exploited by ransomware.
- Strong Passwords: Employing strong, unique passwords for all online accounts and using a password manager to store them securely.
- Multi-Factor Authentication (MFA): Adding an extra layer of security to online accounts by requiring an additional verification step beyond a password.
- Antivirus Software: Installing and maintaining a reputable antivirus program that detects and removes malware, including ransomware.
- Firewall: Utilizing a firewall to block unauthorized access to the computer and its network.
- Backup Strategy: Regularly backing up important data to an external drive or cloud storage service, ensuring data recovery even if ransomware encrypts files.
- Educate Users: Training users to recognize phishing emails, avoid suspicious websites, and exercise caution when downloading files.
The Art of Recovery: Strategies for Ransomware Removal
If ransomware has infiltrated your system, immediate action is crucial. While no method guarantees complete recovery, the following steps can help mitigate the damage:
- Disconnect from the Network: Disconnect the infected computer from the internet and any network to prevent the ransomware from spreading to other devices.
- Isolate the Infected Device: If possible, physically disconnect the infected device from other computers and external drives to avoid contamination.
- Identify the Ransomware: Determine the type of ransomware involved by analyzing the ransom note or researching the symptoms observed.
- Scan with Antivirus Software: Run a comprehensive scan with a reputable antivirus program to detect and remove the ransomware if possible.
- Consider Professional Help: If the antivirus scan fails to remove the ransomware or if the encryption is sophisticated, consider seeking assistance from a cybersecurity professional or ransomware removal specialist.
The Role of Data Recovery: Restoring Lost Files
Even if the ransomware is removed, the encrypted files remain inaccessible. Data recovery options are available, but their success rate varies depending on the complexity of the encryption and the type of ransomware.
- Data Recovery Software: Specialized data recovery software can sometimes recover files from encrypted storage, but success is not guaranteed.
- Shadow Copies: Windows creates automatic backups, known as shadow copies, that can be used to restore files from a point in time before the infection.
- Cloud Storage: If data is backed up to a cloud service, it can be restored to a clean device.
The Importance of Patience and Prudence:
Ransomware removal is a delicate process that requires patience and caution. Avoid paying the ransom, as it encourages cybercriminals and may not guarantee file recovery. Instead, focus on implementing preventative measures, seeking professional assistance if necessary, and exploring data recovery options.
Frequently Asked Questions (FAQs) on Ransomware Removal in Windows 11
1. What are the signs that my computer has been infected with ransomware?
- Files become inaccessible, with file extensions changed or replaced with strange characters.
- A ransom note appears on the screen or is sent via email demanding payment.
- Computer performance slows down significantly, and unusual processes or programs run in the background.
- Antivirus software flags suspicious activity or reports a malware infection.
2. How do I prevent ransomware from infecting my computer?
- Keep your operating system and software applications updated with the latest security patches.
- Use strong passwords for all online accounts and avoid using the same password for multiple accounts.
- Enable multi-factor authentication for sensitive online accounts.
- Install and maintain a reputable antivirus program.
- Be cautious when opening email attachments or clicking links, especially from unknown senders.
- Avoid visiting suspicious websites or downloading files from untrusted sources.
- Regularly back up your important data to an external drive or cloud storage service.
3. What should I do if my computer has been infected with ransomware?
- Immediately disconnect the infected computer from the internet and any network.
- Isolate the infected device from other computers and external drives.
- Run a comprehensive scan with a reputable antivirus program.
- Consider seeking assistance from a cybersecurity professional or ransomware removal specialist.
- Explore data recovery options, including data recovery software, shadow copies, or cloud storage.
4. Should I pay the ransom?
- Paying the ransom is not recommended. It encourages cybercriminals and does not guarantee file recovery.
- There is no guarantee that the attackers will decrypt your files even after payment.
- Paying the ransom can contribute to further ransomware attacks.
5. What are the best data recovery options for ransomware victims?
- Data recovery software can sometimes recover files from encrypted storage, but success is not guaranteed.
- Shadow copies, automatic backups created by Windows, can be used to restore files from a point in time before the infection.
- Cloud storage can be used to restore files to a clean device if data is backed up to a cloud service.
Tips for Preventing and Mitigating Ransomware Attacks
- Stay Updated: Regularly update your operating system, software applications, and antivirus program to address vulnerabilities.
- Be Cautious: Exercise caution when opening emails, clicking links, or downloading files from unknown sources.
- Backup Regularly: Implement a comprehensive data backup strategy, backing up data to an external drive or cloud storage service.
- Educate Users: Train users to recognize phishing emails, avoid suspicious websites, and practice safe browsing habits.
- Secure Your Network: Use strong passwords and enable multi-factor authentication for all network devices.
- Monitor Activity: Regularly review system logs and security alerts for signs of suspicious activity.
- Limit User Permissions: Restrict user permissions to minimize the impact of a potential ransomware infection.
Conclusion
Ransomware poses a significant threat to individuals and organizations alike. While there is no foolproof defense against this malicious software, proactive measures, robust security practices, and timely action can significantly reduce the risk of infection and minimize the potential damage. By understanding the nature of ransomware, implementing preventive strategies, and exploring data recovery options, users can navigate the digital landscape with greater confidence and resilience. Remember, prevention is the best defense, but preparedness is essential in the face of cyber threats.
![5 Best Ransomware Removal Tools Software 2023 [Windows 11, 10, 7] Get PC Apps](https://www.getpcapps.com/wp-content/uploads/2018/09/Wana-Decrypt0r-2.0-Ransomware-removal-tools-windows-pc.jpg)




Closure
Thus, we hope this article has provided valuable insights into Navigating the Labyrinth: A Comprehensive Guide to Ransomware Removal on Windows 11. We thank you for taking the time to read this article. See you in our next article!
Leave a Reply